- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Adtran Support Community
- :
- Documentation
- :
- Enterprise-Class Wi-Fi
- :
- Elite On-Premises
- :
- vWLAN Quick Deployment and Configuration Guide
vWLAN Quick Deployment and Configuration Guide
vWLAN Quick Deployment and Configuration Guide
Introduction
This document covers quick deployment options for vWLAN in small office/home office (SOHO) installations. This guide covers how to set up basic WiFi network access using password-authenticated SSIDs (WPA2-Personal) as well as firmware and SSID management in vWLAN. For larger deployments with more complex features such as 802.1X, Captive Portal, etc. please see the vWLAN General Deployment Guide . Each feature should be configured in the order shown in this document.
This guide assumes that vWLAN is already accessible via IP through the administrative interface. If you need assistance deploying vWLAN in VMware, please consult the documentation. Please read the for assistance with the physical vWLAN hardware appliance. It is best practice to activate Bluesocket Access Points after configuring vWLAN. However, if you need assistance with activating Bluesocket Access Points, please view the .
Implementation
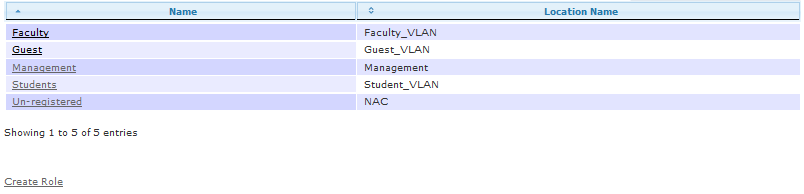
Locations and Location Groups
A location in vWLAN is directly related to the network address, mask, and VLAN tag (when applicable) of a subnet that exists in the network infrastructure. For instance, if a corporate network and guest network are desired to be created, these would each have a location in vWLAN corresponding to their particular subnet in the infrastructure.
Only non-native VLAN locations need to be created in vWLAN prior to installation. The native VLAN for each AP will automatically create a corresponding location named vLoc. For instance, when using a single network for wireless access, no locations would need to be manually created if the native VLAN will be used.
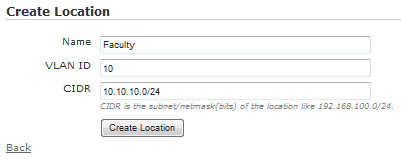
Locations in vWLAN are found under Configuration > Role Based Access Control > Locations. To create a location, click Create Location, or click the location name if you need to edit an existing location.
Input an appropriate Name for the location, assign the VLAN ID, and input the CIDR (this will be in <ip address>/<bit mask> as shown below)
Once locations are configured, the Status > Locations screen should indicate what locations are ACTIVE and which of the BSAPs discovered which locations. If a location is not ACTIVE, or a BSAP does not appear in the Access Points list, then check the switch configurations to make sure ports have been properly configured to support 802.1Q. Also verify that a DHCP scope has been created for the subnet (see How does location discovery work on the vWLAN? for more details)
Services and Destination Groups
vWLAN possesses the ability to control client traffic with a firewall process on each AP that is based on who a client is (determined by Roles, as discussed in the next section). For instance, a corporate network for WiFi access may allow all traffic to traverse the network, but a guest network may block certain services to internal destinations. To create these firewall rules (displayed in the next section), services (the protocol being specified) and destinations (IP address or network the traffic is destined for) may need to be created.
Note: If you have internal filtering for these subnets, you do not have to configure firewall rules in the AP.
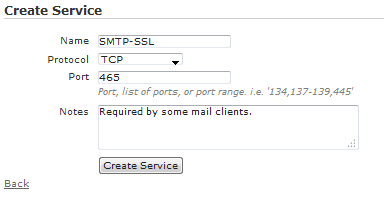
Services are located under Configuration > Role Based Access Control > Services. Note that many common services are already created. To create a new one, click Create Service at the bottom. Input an appropriate Name for the service. The Protocol drop-down menu will list the supported protocols available. If the protocol selected requires a port number, then fill out the Port field. Add any Notes which might help describe the service, and click Create or Update service.
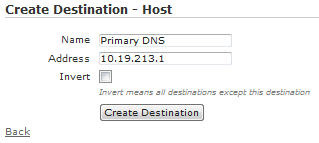
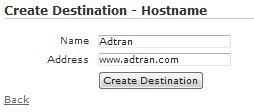
There are three (3) types of destinations (host, hostname, and network), all of which can be configured under Configuration > Role Based Access Control > Destinations. Click the name of existing destination to edit, or choose one of the Create links for the appropriate type.
A destination host is a single IP address, or host, but not a hostname. A destination host is the most basic type. You can configure a Name and Address for destination hosts. The address should be a single IP address.
A destination hostname is generally used if configuring a captive portal. For more information, please see the .
A Destination Network requires a Name, network Address, and Netmask. The Address must be a valid network address, not a host address, for the Netmask being used. For example, 10.10.10.0 is a valid entry when using 255.255.255.0, but 10.10.10.128 is not. Even though 10.10.10.128 is a valid host address, it is not the network address given the Netmask of 255.255.255.0.
Roles
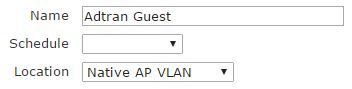
Roles control what properties and network ability different clients are given when they connect to a wireless network. Generally roles will have a 1:1 relationship to an SSID. For instance, the corporate SSID might have a role called “Corporate” allowing full access, while a Guest SSID would have a role called “Guest” allowing access only to the internet or certain web pages. To create a role, click Create Role on the Configuration > Role Based Access Control > Roles page.
Start off by choosing an appropriate Name and Location for the role. In this example
Next, the Firewall Rules need to be defined. New firewall rules can be added by clicking Append Firewall Rule, and each row can be moved up or down by clicking and dragging the arrows to the left of each row. Each column is presented as a drop-down menu where defined values or previously configured items can be selected. There is an implicit deny rule at the bottom of the firewall rules, so it is not required to explicitly define a rule for this.
The firewall rules are processed in a top-down fashion, so it is important keep track of what is being allowed or denied above any additional rules that are configured. For example, if the desire is to deny traffic to a single network, but allow all traffic to any other destination, this can be done by configuring a deny rule first followed by an allow any rule.
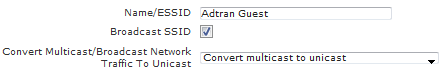
Service Set Identifiers (SSIDs)
SSIDs are located under Configuration > Wireless > SSIDs. The Name/ESSID is the most noticeable and familiar aspect of a wireless network. This is the name that will display in a client’s wireless network list. The Broadcast SSID option does not enable/disable the SSID, but rather it hides the SSID.
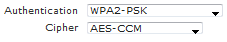
Authentication controls access to the network. The Cipher determines how client traffic will be encrypted. For the purposes of this document, WPA-2PSK with AES-CCM is being configured.
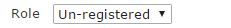
Role defines which set of firewall rules are applied to an authenticated user, as well as configure the AP to tag the traffic into the correct Location. By default, when a new SSID is created it is assigned to the Un-registered Role until the value is changed.
If you need more sophisticated authentications like LDAP, 802.1X, or Captive Portal please see please see the .
AP Templates
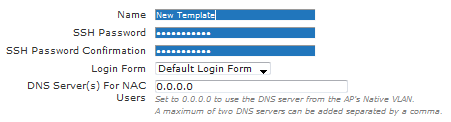
The AP template is the actual BSAP configuration. AP templates can be edited or configured under Configuration > Wireless > AP Templates. For basic deployments, just use the default template as it will be automatically assigned to all APs. You will start by supplying a Name and SSH Password. The default SSH password is blue1socket, and this field can be left unmodified. The Login Form here will act as a default for all SSIDs unless the SSID has been explicitly configured with a unique form. The DNS Server(s) For NAC Users refers to Un-registered users who must use Captive Portal authentication.
Be sure to select the AP firmware in the AP template. The BSAPs cannot receive their configuration if the firmware is not selected in the template, and they will reboot continuously until the firmware image is selected. If no AP firmware is uploaded to vWLAN, then the drop-down menu will be blank. AP firmware can be uploaded in Configuration > Wireless > AP Firmware, and firmware can be applied to all templates when it is uploaded.
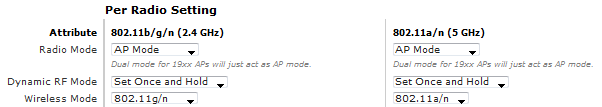
After selecting the firmware, confirm the Per Radio Setting fields. The Radio Mode should be set to “AP Mode” to allow client connections. The following settings are recommended.
![]() sign in the right pane of the SSID field and then save the template. Once this is done, you should see a “1” next to the section labeled “Domain Tasks” in the top right corner. Click this link and you will see a domain task asking to update the configuration on the APs. Click this and it will automatically update the APs and wireless service should be configured. Status of the APs, locations, etc. can be checked in the Status section of vWLAN to troubleshoot any issues.
sign in the right pane of the SSID field and then save the template. Once this is done, you should see a “1” next to the section labeled “Domain Tasks” in the top right corner. Click this link and you will see a domain task asking to update the configuration on the APs. Click this and it will automatically update the APs and wireless service should be configured. Status of the APs, locations, etc. can be checked in the Status section of vWLAN to troubleshoot any issues.
Useful Links
- Administrator's Guide vWLAN Version 2.2.1 and Later
- VMware Quick Start Guide vWLAN Version 2.2.1 and Later
- vWLAN Hardware Appliance (1st Gen) Quick Start Guide
- Bluesocket Access Point (BSAP) Troubleshooting Guide
- Switch Provisioning Best Practices
- Configuring the Firewall (IPv4) in AOS
- How does location discovery work on the vWLAN?
- Configuring DHCP in AOS
- vWLAN External RADIUS-802.1X Authentication
- vWLAN Single Click Customized Login Page
-
 Anonymous
Anonymous