- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Adtran Support Community
- :
- Documentation
- :
- ADTRAN Operating System - AOS
- :
- General
- :
- Configuring a VPN to the Amazon Cloud
Configuring a VPN to the Amazon Cloud
Configuring a VPN to the Amazon Cloud
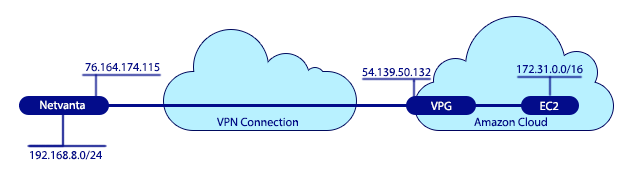
This document will cover how to connect to Amazon's Virtual Private Cloud (VPC) using AOS devices. Computers at the local side of the connection will be able to use the VPN tunnel to reach the Amazon Virtual Private Cloud (VPC) and communicate with the remote servers (EC2 instances) set up there.
Hardware and Software Requirements and Limitations
Hardware and Software Requirements and Limitations
This configuration guide is applicable to ADTRAN AOS devices running the enhanced feature pack version of AOS, allowing for VPN connectivity. Only static route VPN connections can be used with this, dynamic routing protocols can not be used with this tunnel.
Before beginning VPN configuration, an EC2 instance should already be setup in the Virtual Private Cloud (VPC). On the AOS side, the VPN tunnel must be configured for main mode. This document will cover how to set up the VPN as it pertains to connecting to Amazon's VPC. The guide, Configuring a VPN using Main Mode, can be referenced for more information on how to configure a Main Mode VPN tunnel in AOS.
1. VPC configuration.
a. Go to the AWS Console and then to VPC.
b. In the left column under VPN Connections go to Virtual Private Gateways.
c. Click 'Create Virtual Private Gateway'.
d. Enter the name for the Gateway.
e. Click the 'Yes, Create' button.
f. Select the gateway and click 'Attach to VPC'.
g. Select the VPC in the dropdown and click the 'Yes, Attach' button.
h. Wait a little and it will show up as 'Attached'.
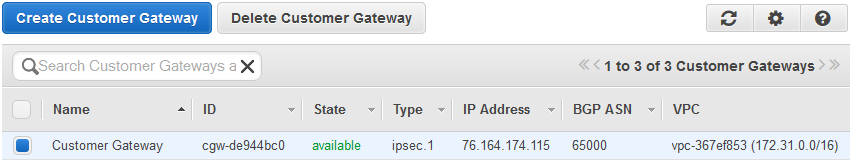
2. Customer Gateway
a. Go to Customer Gateway, right above Virtual Private Gateways.
b. Click 'Create Customer Gateway'.
c. Enter the information for the AOS device.
i. Name Tag will be the name used for the device.
ii. Routing has to be set static.
iii. Ip Address is the public ip address of the AOS device. Look under Data then IP interfaces if the ip address needed is unclear.
iv. Click on the 'Yes, Create' button. After it’s done the Gateway will appear as ‘available’.
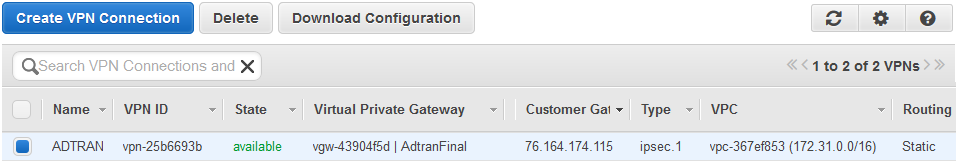
3. VPN configuration
a. Click 'VPN Connections', it can be found beneath Virtual Private Gateways.
b. Click on the 'create VPN Connection' button.
c. For Name Tag enter the name for the VPN connection.
d. The Virtual Private Gateway is the VPG created in step 1.
e. Routing Options must be set to static.
f. Static Prefixes are the local network (e.g. 192.168.8.1/24).
g. Click the 'Yes, Create' button.
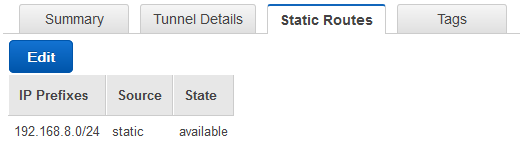
h. If an error message appears saying the static route could not be added, then wait until the VPN state is available then select it. Go to the Static Routes tab at the bottom. Click 'Edit' to add the local network and click 'Save'.
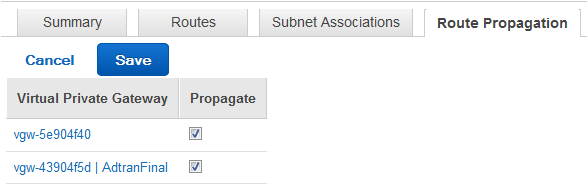
4. Route Tables
a. Since static routes are required its necessary to ensure the LAN network is propagated properly. Go to Route Table and select the proper Route Table ID.
b. Click on Route Propagation and make sure the VPG is set 'Yes' under Propagation.
c. If it's not, click on 'Edit' and put a check mark under Propagate for the VPG and 'Save'.
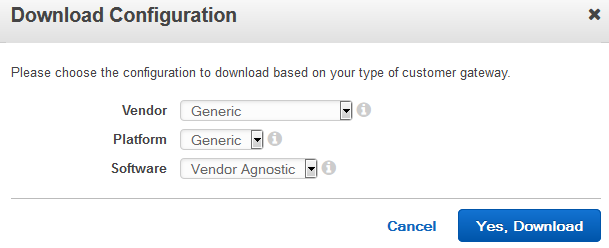
5. Download Configuration
a. A copy of the Amazon Configuration will be required to continue. Look in VPN Connections, Download Configuration can be seen at the top. Click that and use the following settings.
b. For Tunnel #1 get the Pre-Shared Key and the IP address of the Virtual Private Gateway. These two bits of information are required for configuring the Adtran.
1. Before you start.
Amazon provides the same VPN requirements for every tunnel, aside from the peer, the Pre-Shared Key, and private networks that match the VPN selectors. You can find your private network on the Amazon side by going to 'Your VPVs' and then looking at the VPC CIDR. You can use the following configuration information on your Adtran as it is, except where otherwise indicated.
2. Configuration using the GUI
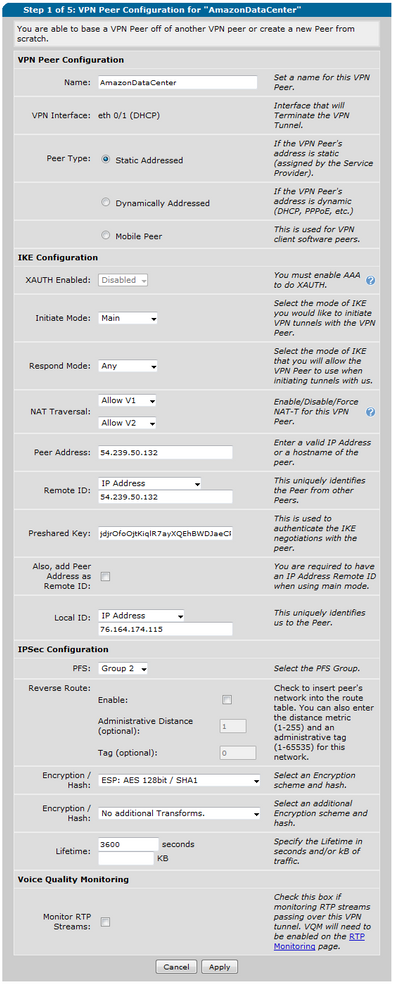
Creating your VPN in the GUI is straightforward. Go to Data then to VPN peers. Create a new peer. Then configure it as follow
b. Your IKE settings are configured here. It will always be AES-128 and Sha with Diffie Hellman Group 2.
c. The local IP subnet is your local network. In this example my router is configured with 192.168.8.0/24.
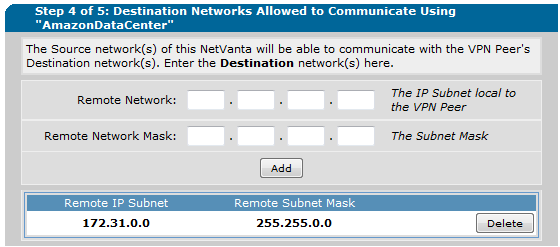
d. The Remote IP subnet is the network on the Amazon side. If there is any question of this look at the Customer Gateway above where the VPC is listed as 172.31.0.0/16.
3. Configuration using the CLI
a. Here’s a sample configuration for command line. Just fill in the information for your Amazon connection where relevant.
crypto ike policy 100
initiate main
respond anymode
local-id address 76.164.174.115
peer YOUR-AMAZON-PUBLIC-ADDRESS
attribute 4
encryption aes-128-cbc
authentication pre-share
group 2
crypto ike remote-id address YOUR-AMAZON-PUBLIC-ADDRESS preshared-key YOUR-PRESHARED-KEY ike-policy 100 crypto map VPN 100 no-mode-config no-xauth
ip crypto map VPN 100 ipsec-ike
description AmazonDataCenter
match address ip VPN-100-vpn-selectors
set peer YOUR-AMAZON-PUBLIC-ADDRESS
set transform-set esp-aes-128-cbc-esp-sha-hmac
set security-association lifetime seconds 3600
set pfs group2
ike-policy 100
ip access-list extended VPN-100-vpn-selectors
permit ip 192.168.8.0 0.0.0.255 172.31.0.0 0.0.255.255
a. Add 'crypto map VPN' to your WAN interface.
b. Add 'allow list VPN-100-vpn-selectors stateless' to your local policy-class. Add 'allow reverse list VPN-100-vpn-selectors stateless' to your WAN policy-class. Put them both at the top of their policy class.
You can ping from within the Adtran to bring up the tunnel. Just do 'ping <private ip address on your EC2 instance> source <private ip address on the AOS device>. In the example configuration above it might look like 'ping 172.31.31.31 source 192.168.8.1'. This creates traffic to match the VPN selectors. If you can ping successfully to your EC2 instance then you will be connected. At this point the VPN should show as up in the AOS device and on the Amazon side.
The VPN should show as up in the GUI. You can see this in command line as well. The commands 'sho crypto ike sa' and 'sho crypto ipsec sa' will show if the VPN security associations have been created.
There's no troubleshooting you can do on the Amazon side. Debug crypto ike neg on the Adtran side should tell us how far the negotiation is getting.
For detailed instructions on troubleshooting the VPN check out our Guide to Main Mode VPN. There is a troubleshooting section at the end that has the steps to go through.
-
 Anonymous
Anonymous