- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 1300 Series
- :
- Block port 25 from all computers except server on nat configured interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Block port 25 from all computers except server on nat configured interface
I would like to block all outbound traffic originating from port 25 for all computers on the network except the server which is supposed to be relaying SMTP email. I expected this to be fairly easy, just add a traffic selector to the NAT policy of the Private Security zone, however, in the web interface, when I go to the "NAT list wizard-ics" policy in the Private security zone, I am not given the option to specify ports when adding additional traffic selectors. Is this one of those things that cannot be done from the web interface for some reason, or am I simply missing something in the policy configuration? This is the default NAT policy that was initially setup by the wizard.
This is a NetVanta 1335 PoE running firmware version 18.02.01.00.E
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Block port 25 from all computers except server on nat configured interface
Hi telarin:
This can be done in the CLI or GUI. The important thing to remember is that the firewall policies are processed top-down. The CLI and GUI list policies in the order they are applied. When traffic matches a policy, action is taken. There is no need for the firewall to continue down the list for that particular traffic, once a match is found and action taken. In your case, the firewall should perform the following actions in the order listed:
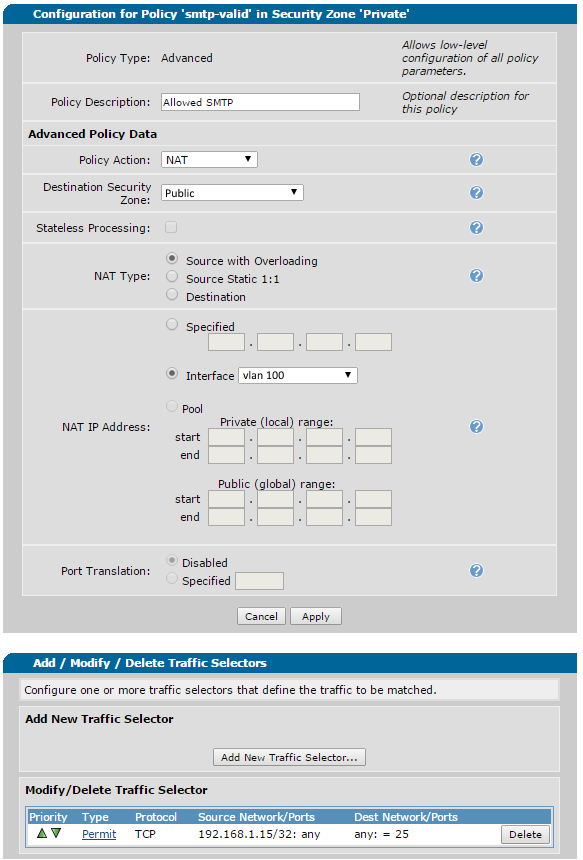
- NAT outbound valid SMTP traffic (sourced from your mail server)
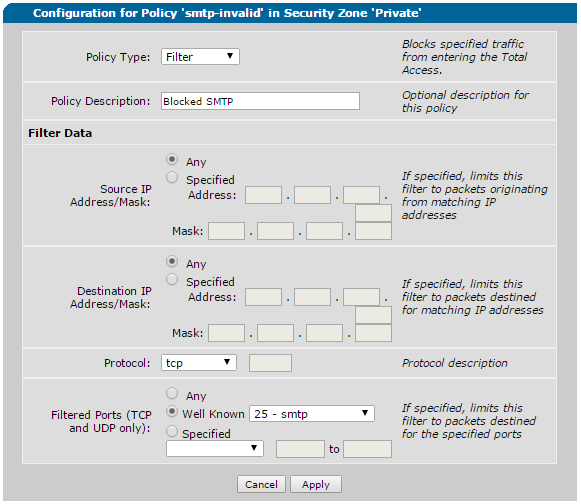
- Block invalid SMTP traffic (not sourced from your mail server)
- NAT outbound all other internet traffic
Here's an example from the CLI that can be modified to fit your specific mail server address, policy-classes, etc. Note the policy order in the Private policy-class:
!
ip access-list standard wizard-ics
remark NAT list wizard-ics
permit any
!
!
ip access-list extended smtp-invalid
remark Blocked SMTP
permit tcp any any eq smtp log
!
ip access-list extended smtp-valid
remark Allowed SMTP
permit tcp host 192.168.1.15 any eq smtp log
!
!
ip policy-class Private
nat source list smtp-valid interface vlan 100 overload policy Public
discard list smtp-invalid
nat source list wizard-ics interface vlan 100 overload policy Public
!
Here's an example 'Allowed' ACL from the GUI:
And an example 'Blocked' ACL:
Just make sure the Allowed policy is higher in your security zone rule list than the Blocked policy, and both are higher than the general NAT overload (wizard-ICS) policy.
It's worth considering an AOS upgrade to your 1335. That unit supports the latest maintenance release (R11.4 as of this post). AOS 18.X is no longer eligible for support. AOS R11.4 includes many bug fixes and enhancements and is highly recommended!
Best,
Chris