- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 1500/1600 Series (AOS)
- :
- 802.1x port authentication with voice vlan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
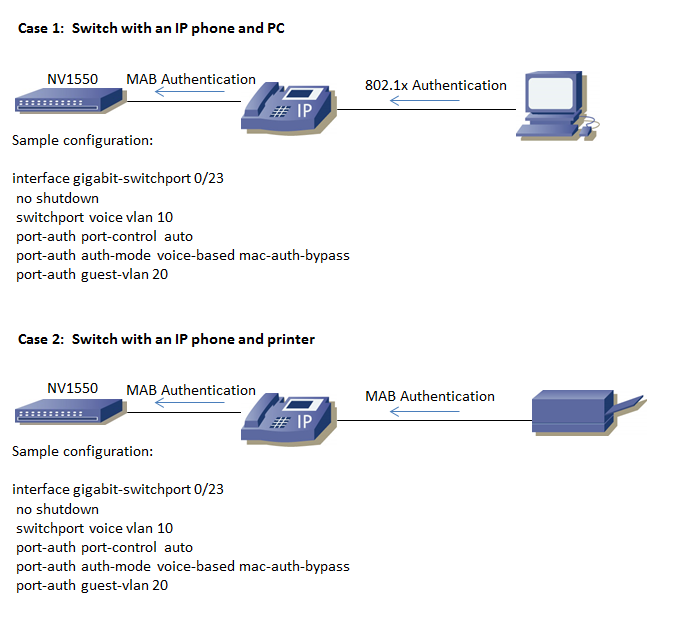
802.1x port authentication with voice vlan
Hi Just wondering if someone can help me i am trying to configure 802.1x authentication and its not working. We are using Netvanta 1648p and 1500's
Here is example config that is not working. There is a lot of cisco configuration examples but nothing for adtran.
interface gigabit-switchport 0/2
description IP_Phones
spanning-tree edgeport
no shutdown
switchport access vlan 10
switchport voice vlan 200
qos trust cos
port-auth auth-mode voice-based mac-auth-bypass
port-auth port-control auto
Here is normal setup without port authentication.
interface gigabit-switchport 0/1
description IP_Phones
spanning-tree edgeport
no shutdown
switchport mode trunk
switchport trunk native vlan 10
switchport voice vlan 200
qos trust cos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: 802.1x port authentication with voice vlan
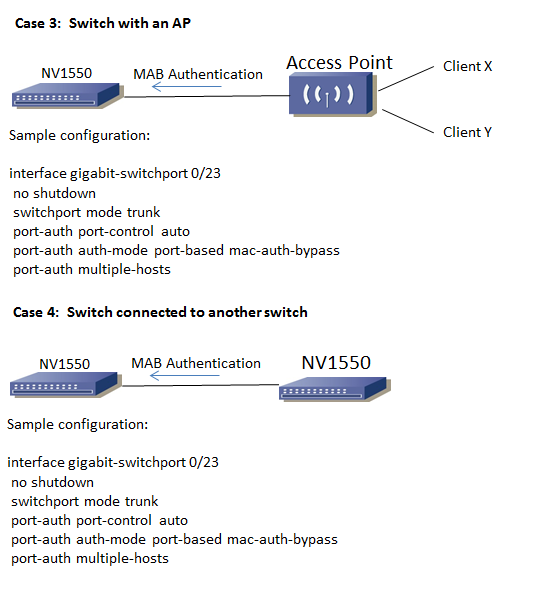
There are many 802.1X configurations possible -
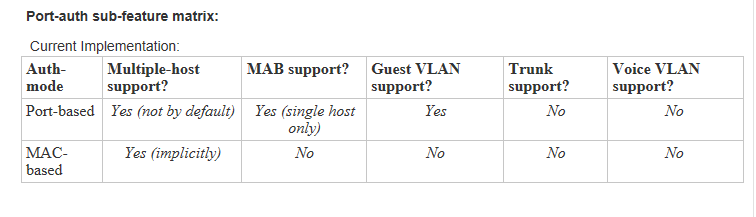
With support a Maximum of two MAC address for each port, or one MAC address with all others being passed through ( as in case 3 or 4 )
FAQs
Q1: In scenarios 1 and 2, what happens if the RADIUS assigned VLAN (for the PC or printer) is different from the configured access VLAN?
A1:
Configured access VLAN | Configured Voice VLAN | RADIUS assigned VLAN | Guest VLAN | Dynamic VLAN for the PC/printer |
A | V | A | n/a | A (untagged) |
A | V | B | n/a | B (untagged) |
A | V | No vlan specified | n/a | A (untagged) |
A | V | Failed authentication | C | C (authorized, untagged) |
A | V | Failed authentication | none | none (unauthorized) |
A | V | V | n/a | V (authorized, tagged) |
Note: The running-config does not change. A user will need to look at the output of “show port-auth interface” to determine the dynamically assigned VLAN.
Q2. In scenarios 1 and 2, what happens if the RADIUS assigned VLAN (for the phone) is different from the configured voice VLAN?
A2. Refer to table in Q1.
Note: In a case of VLAN conflict, the RADIUS server assignment always supersedes the locally configured setting.
Q3. What happens when the first device that connects (phone/PC/printer) gets placed into the Guest VLAN in scenarios 1 and 2?
A3. Since we only allow 1 MAC to be learned on the untagged (access) VLAN, the second device will never be able to authenticate on the untagged VLAN. The Guest VLAN is treated like the untagged VLAN on a voice VLAN enabled port. If a rogue phone is placed on the Guest VLAN, no other devices sitting behind it will be able to gain access to the same Guest VLAN and will remain in an unauthorized state.
NOTE: If an EAP packet comes in from the second device, the port-auth state machine will be restarted, causing the first device to lose connectivity.
Q4. In scenario 2, how does a user replace the printer behind the phone with another non-EAP device if the original device has already been authenticated?
A4. The authenticator, i.e. the AOS switch, has no indication that the device behind the phone has been disconnected. Hence, the switch will preserve the original authenticated MAC in its MAC-table. The downside to this is that any new (non-EAP) device that is connected in the printers' place will remain unauthorized until the port is bounced. The port-auth state machine would need to be somehow restarted in order for the new device to be authenticated. In the real world, the user would be expected to reboot her phone to re-establish connectivity on the new device. This caveat only applies to non-EAP devices since an EAP device will transmit EAP packets that will automatically trigger a restart of the port-auth state machine.
Q5. Why does the Polycom VVX 300/400/500 not obtain an IP address even after being authenticated by the switch in voice-based MAB mode?
A5. Polycom phones usually send out a finite number of DHCP Discover messages (9, in some cases) before giving up. If the phone has not been authenticated before the DHCP client times out, it will never acquire an IP address unless it is rebooted. The default Port-Auth Timeout TX-period (wait time between identity requests) is 30 seconds. MAB takes 3 times the timeout period to kick in and authenticate the phone, so if the phone quits sending DHCP Discovers after 90 seconds, the phone will never establish IP connectivity. The workaround here is to lower the Port-Auth Timeout TX-period (global setting) to 7 seconds. In the case of the NV1550, this timeout needs to be lowered even further to 4 seconds.
Q6. Is Guest VLAN supported in scenarios 3 and 4 (Port-based over Trunk)?
A6. No, it becomes a security vulnerability if multiple-host is enabled. This would allow all devices sitting behind the Agg Swx or AP to gain network access.
Q7. What happens when a printer is connected to a hub that already had an authenticated PC sitting behind an authenticated MAB phone?
A7. In the case of the Polycom VVX 300, 400 and 500, it will cause the phone to reset.
Q8. Why can I not ping my port-based authorized agg switch from my authenticator in scenario 4?
A8. When a switch port is configured for port-auth auth-mode port-based while attached to something other than a router, port-auth multiple-hosts is going to have to be turned on. This is because in the case that the port is connected to another switch, we are trying to authorize the port mac without the cpu mac causing us to be unable to ping. But enabling port-auth multiple-hosts allows the port to authorize both the port mac and the cpu mac allowing the pings to come through.
Q9. After voice-based authentication authorizes,why doesn't my LLDP-MED capable phone obtain an IP address from DHCP?
A9. We have found that on some units, a user will have to adjust the port-auth timeout tx-period global configuration. This has to happen because some phones will stop trying to obtain an ip address before port-auth has finished authorizing. For the 1550, we recommend setting the global configuration to "port-auth timeout tx-period 4."
Q10. Under what conditions can "port-auth multiple-host" be configured?
A10. The port has to be either:
- in Access mode and configured for Port-based port-auth, or
- in Trunk mode and configured for Port-based MAB
NOTE: All other conditions will result in an error message.
Q11. Can an authorized phone acquire an IP address on the Access/Guest VLAN when connected to a voice-based MAB port?
A11. No, LLDP-MED capable phones will not transmit DHCP discover messages on the access/guest VLAN and hence, never acquire an IP address.
Q12. Why does a supplicant not acquire an IP address from the internal AOS DHCP server when moved to a different VLAN via Port-auth?
A12. A binding already exists for the current VLAN on the AOS DHCP server, so the binding table needs to be cleared before a new IP on the new VLAN (for the same source MAC) can be assigned.
See the following for more detailed information -