- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 1500/1600 Series (AOS)
- :
- Securing LL3 Switch with Public IP Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Securing LL3 Switch with Public IP Access
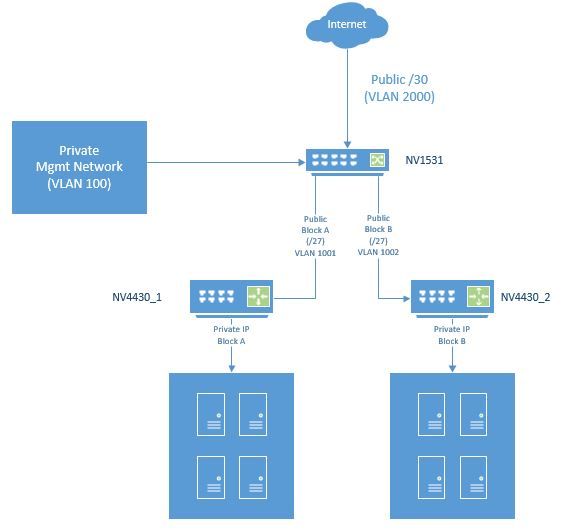
I need to use a NV1531 (LL3 Switch) to terminate a Public Internet Connection (Fiber). The NV1531 is then connected to NV4430 routers which will do all the heavy routing/NAT/firewalling activities for the main private networks. I need to properly secure the NV1531, but also still provide some way of managing it without having to physical be consoled into it. I believe that I need to use HW ACLs and HW Maps, but want to confirm. I need the NV1531 to serve in a Layer 3 mode on the Public side, so I can expand additional Public Subnets "stacks" that need isolated as shown into the future.
My goals are as follows:
1. Secure NV1531 from unlawful internet access. I only want to have HTTPS and SSH access to the switch from a couple Public IP ranges coming in on VLAN 2000.
2. Allow access on HTTPS and SSH coming from a couple Hosts Publics that will come into the switch on VLAN 1001 and VLAN 1002.
3. Allow access on HTTPS and SSH coming from the private VLAN100 management network. Also allow SNMP access to the switch from the same VLAN 100 management network.
4. Deny access to the switch from all other locations except console access.
5. Allow traffic to flow in/out from Internet through switches to the two separate NV4430 routers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Securing LL3 Switch with Public IP Access
To secure the control plane:
service password-encryption
[TACACS/RADIUS/Local username authentication as appropriate]
ip access-list standard admin-access
permit host aa.bb.cc.dd
permit host ee.ff.gg.hh
ip access-list standard snmp-acess
permit host ww.xx.yy.zz
no http server
http secure-server
http ip secure-access-class admin-access in
snmp-server community itsasecret RO ip access-class snmp-access
line telnet 0 4
shutdown
line ssh 0 4
ip access-class admin-access in
no shutdown
Enable IP routing, route VLANs 1001, 1002, 2000 as appropriate.
Configure anti-spoofing BCP38/RFC2827 access-policies on VLAN interfacess 1001,1002,2000
For your management VLAN 100 interface, configure an access-policy to permit self only and deny all other .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Securing LL3 Switch with Public IP Access
Thank you jayh for the response. I'll be working on implementing this tomorrow, but would appreciate clarification on the following if you have time.
jayh wrote:
For your management VLAN 100 interface, configure an access-policy to permit self only and deny all other .
To my knowledge, the only way to accomplish this on the LL3 Switch is to use HW ACLS/HW Maps. I'm familiar with using "self" on ACPs in the routers, but is that an option in HW Maps? My thinking is to accomplish this I would do the following:
ip hw-access-list extended TRUST_VLAN100
permit host mm.nn.oo.pp host qq.rr.ss.tt
hw-access-map TRUSTMAP_VLAN100
vlan 100
forward ip TRUST_VLAN100
jayh wrote:
Configure anti-spoofing BCP38/RFC2827 access-policies on VLAN interfaces 1001,1002,2000
I thought this was built in, but may be mistaken. Can you elaborate?
jayh wrote:
Enable IP routing, route VLANs 1001, 1002, 2000 as appropriate.
To "Enable IP routing" one just really needs the following included in the LL3 switch config:
ip default gateway ww.xx.yy.zz
!
ip routing
!
interface vlan 1001
ip address hh.gg.jj.kk
!
(repeat for interface VLANs 1002 and 2000)
!
ip route 0.0.0.0 0.0.0.0 ww.xx.yy.zz