- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 6000 Series
- :
- QoS maps and interfaces
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First Question: A QoS map that matches on DSCP tag as well as an ACL > is it and AND or OR operation? Will it only match traffic that matches BOTH the ACL and DSCP tag or will it match traffic with a DSCP tag of 26 that's IP source is outside of the ACL scope? >> see configuration below.
qos map map1 1
match dscp 26
match list MediaSource
interface eth 0/1
ip address 1.1.1.1 255.255.255.240
media-gateway ip primary
qos-policy out map1
no shutdown
ip access-list extended MediaSource
permit udp 2.2.2.2 0.0.0.255 any
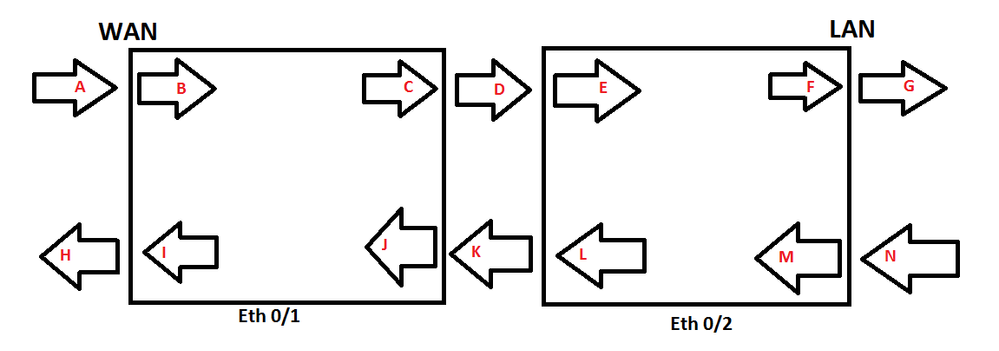
Second Question: Is there a good place to get an explanation of the Inbound and Outbound QoS policy's on an interface? I applied this policy to the inbound side of the WAN interface...this didn't seem to be matching the traffic from the outside, only had a few packet matches, when I applied it to the outbound policy it had thousands of matches. I've attched a diagram that would represent each of the interfaces. Which letter (see image) would correspond to eth 0/1 inbound and eth 0/1 outbound?
Thanks!
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Andrew,
Thanks for posting in our Support Community. By default, the match statements are a logical OR operation. However, you can modify that behavior with an optional keyword as shown below. This would allow you to use a logical AND operation regarding your match statements.
(config)#qos map myMap 10 match-all
In your diagram, the A arrow would correspond to the inbound QoS and the H arrow would correspond to the outbound QoS. Stated a different way, consider QoS policies to be an outer shell for the unit. The best way to describe an Inbound QoS policy is to say that it allows you to match and mark traffic as it comes into the interface. An outbound QoS policy allows you to match, mark, and prioritize/queue traffic as it leaves the interface.
Generally speaking, inbound QoS polices are used to mark traffic, often so that QoS queuing can be specified in the outbound policy on the egress interface. The inbound marking is important because after the NAT process, for example, traffic becomes more difficult to differentiate. I believe that the best way to understand the use of inbound QoS policies is to study the example from Configuring QoS in AOS on pages 40-42. I have copied it below for you to reference. In this example, traffic from different tenants is marked with a different DSCP value so that we can easily reference each of those tenants in the outbound QoS map, even though the NAT process has taken place.
Thanks!
David
ip firewall
!
qos map SET-DSCP 10
match list CUSTOMER1
set dscp af11
qos map SET-DSCP 20
match list CUSTOMER2
set dscp af21
qos map SET-DSCP 30
match list CUSTOMER3
set dscp af31
!
qos map SHAPE-OUT 10
match dscp af11
shape average 400000
qos map SHAPE-OUT 20
match dscp af21
shape average 400000
qos map SHAPE-OUT 30
match dscp af31
shape average 400000
!
interface eth 0/1
ip address 192.168.1.1 255.255.255.0
ip address 192.168.2.1 255.255.255.0 secondary
ip address 192.168.3.1 255.255.255.0 secondary
access-policy Private
qos-policy in SET-DSCP
no shutdown
!
interface t1 1/1
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface ppp 1
ip address 208.61.209.1 255.255.255.252
access-policy Public
qos-policy out SHAPE-OUT
no shutdown
cross-connect 1 t1 1/1 1 ppp 1
!
ip access-list standard wizard-ics
remark Internet Connection Sharing
permit any
ip access-list extended CUSTOMER1
permit ip 192.168.1.0 0.0.0.255 any
!
ip access-list extended CUSTOMER2
permit ip 192.168.2.0 0.0.0.255 any
!
ip access-list extended CUSTOMER3
permit ip 192.168.3.0 0.0.0.255 any
!
ip access-list extended NO-INTERNAL-TRAFFIC
permit ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255
!
ip policy-class Private
allow list self self
discard list NO-INTERNAL-TRAFFIC
nat source list wizard-ics interface ppp 1 overload
!
ip policy-class Public
!
ip route 0.0.0.0 0.0.0.0 208.61.209.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Andrew,
Thanks for posting in our Support Community. By default, the match statements are a logical OR operation. However, you can modify that behavior with an optional keyword as shown below. This would allow you to use a logical AND operation regarding your match statements.
(config)#qos map myMap 10 match-all
In your diagram, the A arrow would correspond to the inbound QoS and the H arrow would correspond to the outbound QoS. Stated a different way, consider QoS policies to be an outer shell for the unit. The best way to describe an Inbound QoS policy is to say that it allows you to match and mark traffic as it comes into the interface. An outbound QoS policy allows you to match, mark, and prioritize/queue traffic as it leaves the interface.
Generally speaking, inbound QoS polices are used to mark traffic, often so that QoS queuing can be specified in the outbound policy on the egress interface. The inbound marking is important because after the NAT process, for example, traffic becomes more difficult to differentiate. I believe that the best way to understand the use of inbound QoS policies is to study the example from Configuring QoS in AOS on pages 40-42. I have copied it below for you to reference. In this example, traffic from different tenants is marked with a different DSCP value so that we can easily reference each of those tenants in the outbound QoS map, even though the NAT process has taken place.
Thanks!
David
ip firewall
!
qos map SET-DSCP 10
match list CUSTOMER1
set dscp af11
qos map SET-DSCP 20
match list CUSTOMER2
set dscp af21
qos map SET-DSCP 30
match list CUSTOMER3
set dscp af31
!
qos map SHAPE-OUT 10
match dscp af11
shape average 400000
qos map SHAPE-OUT 20
match dscp af21
shape average 400000
qos map SHAPE-OUT 30
match dscp af31
shape average 400000
!
interface eth 0/1
ip address 192.168.1.1 255.255.255.0
ip address 192.168.2.1 255.255.255.0 secondary
ip address 192.168.3.1 255.255.255.0 secondary
access-policy Private
qos-policy in SET-DSCP
no shutdown
!
interface t1 1/1
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface ppp 1
ip address 208.61.209.1 255.255.255.252
access-policy Public
qos-policy out SHAPE-OUT
no shutdown
cross-connect 1 t1 1/1 1 ppp 1
!
ip access-list standard wizard-ics
remark Internet Connection Sharing
permit any
ip access-list extended CUSTOMER1
permit ip 192.168.1.0 0.0.0.255 any
!
ip access-list extended CUSTOMER2
permit ip 192.168.2.0 0.0.0.255 any
!
ip access-list extended CUSTOMER3
permit ip 192.168.3.0 0.0.0.255 any
!
ip access-list extended NO-INTERNAL-TRAFFIC
permit ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255
!
ip policy-class Private
allow list self self
discard list NO-INTERNAL-TRAFFIC
nat source list wizard-ics interface ppp 1 overload
!
ip policy-class Public
!
ip route 0.0.0.0 0.0.0.0 208.61.209.2