- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 3100 Series
- :
- Re: IPSec Remote Access VPN - No Traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello All,
I am new to Netvanta routers / firewalls. Just tried to setup a quick remote access VPN using Shrewsoft VPN client on a 3140 running NV3140A-R12-2-0-E and I am running into issues.
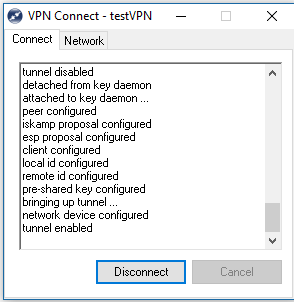
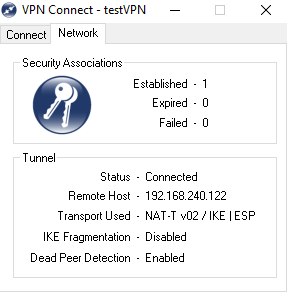
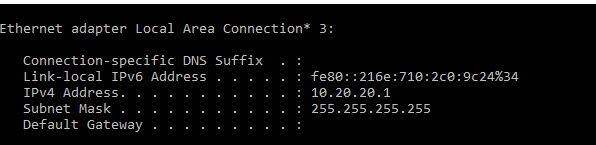
The tunnel forms successfully, the VPN client and the windows laptop show install of route to the VPN subnets behind the firewall, thru the VPN virtual adapter.
Show crypto ike sa and show ip crypto ipsec sa, all show expected outputs, however no traffic passes (TX and RX are shown 0 bytes) from the VPN client to the inside private network.
Here is the relevant lab setup configuration.and some outputs. Please review and advise if I am doing something fundamentally wrong.
ip crypto
ip crypto ffe
crypto ike client configuration pool VPN_USERS
ip-range 10.20.20.1 10.20.20.10
dns-server 8.8.8.8 4.2.2.2
exit
ip access-list extended InternetBoundTraffic
deny ip 192.168.110.0 0.0.0.255 10.20.20.0 0.0.0.255
permit ip any any
exit
ip access-list extended NetMgmt
remark permit Admin Access
permit tcp any any eq https
permit tcp any any eq ssh
permit tcp any any eq telnet
permit tcp any any eq www
permit icmp any any echo
permit icmp any any echo-reply
exit
ip access-list extended VPN_USERS_ACCESS
permit ip 192.168.110.0 0.0.0.255 any
exit
ip policy-class PRIVATE
allow list NetMgmt self
allow list self self
nat source list InternetBoundTraffic interface gigabit-ethernet 0/1 overload
exit
ip policy-class PUBLIC
allow list NetMgmt self
allow list self self
allow reverse list VPN_USERS_ACCESS stateless
exit
crypto ike policy 100
no initiate
respond aggressive
local-id address 192.168.240.122
nat-traversal v1 disable
nat-traversal v2 force
peer any
client configuration pool VPN_USERS
attribute 1
encryption aes-128-cbc
authentication pre-share
exit
ip crypto ipsec transform-set VPNTS esp-aes-128-cbc esp-sha-hmac
mode tunnel
ip crypto map VPNM 10 ipsec-ike
match address ip VPN_USERS_ACCESS
set transform-set VPNTS
reverse-route
ike-policy 100
mobile
exit
crypto ike remote-id any preshared-key labtest1234567890 ike-policy 100 crypto map VPN 10 no-xauth
interface gigabit-eth 0/1
description Internet Port
ip address 192.168.240.122 255.255.255.0
ip access-policy PUBLIC
no shutdown
!
!
interface gigabit-eth 0/2
description LAN Port
ip address 192.168.110.254 255.255.255.0
ip access-policy PRIVATE
no shutdown
!
FW#ping 192.168.110.1
Type CTRL+C to abort.
Legend: '!' = Success, '?' = Unknown host, '$' = Invalid host address
'*' = Request timed out, '-' = Destination host unreachable
'x' = TTL expired in transit, 'e' = Unknown error
'B' = Packet too big
Sending 5, 100-byte ICMP Echos to 192.168.110.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/1 ms
FW#
From VPN Client.
FW#show cry ike sa
Using 1 SAs out of 2000
Peak concurrent SAs: 1
IKE Security Associations:
Peer IP Address: 192.168.240.171
Mode-config Address: 10.20.20.1
Local IP Address: 192.168.240.122
Remote ID: test@test.com
Lifetime: 28815
Status: UP (SA_MATURE)
IKE Policy: 100
NAT-traversal: V2
Detected NAT / Behind NAT: Yes / Yes
Dead Peer Detection: Yes
FW#sh ip cry ipsec sa
2 current IPv4 IPsec SAs on default VRF
2 current IPv4 + IPv6 IPsec SAs on all VRFs (2 peak of 4000 max)
IPsec Security Associations:
Peer IP Address: 192.168.240.122
Mode-config Address: 10.20.20.1
Remote ID: test@test.com
Crypto Map: VPNTS 10
Direction: Inbound
Encapsulation: ESP
SPI: 0x89AE6496 (2309907606)
RX Bytes: 0
Selectors: Src:10.20.20.1/255.255.255.255 Port:ANY Proto:ALL IP
Dst:192.168.110.0/255.255.255.0 Port:ANY Proto:ALL IP
Hard Lifetime: 3580
Soft Lifetime: 0
Out-of-Sequence Errors: 0
Peer IP Address: 192.168.240.171
Mode-config Address: 10.20.20.1
Remote ID: test@test.com
Crypto Map: VPNTS 10
Direction: Outbound
Encapsulation: ESP
SPI: 0x522C1B9E (1378622366)
TX Bytes: 0
Selectors: Src:192.168.110.0/255.255.255.0 Port:ANY Proto:ALL IP
Dst:10.20.20.1/255.255.255.255 Port:ANY Proto:ALL IP
Hard Lifetime: 3580
Soft Lifetime: 3530
Egress MTU: 1367 bytes
FW#
Thanks
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Finally the problem is solved for me;).
I re-installed Shrewsoft latest client using windows 7 compatibility mode and everything is working consistently.
Thank you Wil and Evan for your great support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
dpsharma,
I believe you have all of the necessary configuration except for one small piece. In your private policy class, you will want an Allow at the top to allow the VPN traffic through. So simply add an allow statement for that access list at the top of the Private policy class (it should be stateless as well).
VPN traffic has to be allowed through the firewall to hit the Crypto engine properly. So your ping is just trying to use NAT right now which causes it to be missed by the Crypto map. Let us know the results.
Thanks,
Evan
ADTRAN Product Support Engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
Thanks so much Evan for looking into this for me. I will test late tonight as I am working out of town this week. But I had tested by even removing the policy / ACL from the inside interface. And with policy applied, the drops / discards were zero. I was under the impression that I did not need this on the private interface as firewall will allow the returning traffic, but it might not, and I might have something else wrong when I tested my setup without ACL on inside. Will sure find out later tonight and report back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
Will following make interesting traffic to be exempted from NAT over tunnel or do we need to specifically deny it under the NAT ACL?
ip crypto map VPNM 10 ipsec-ike
match address ip VPN_USERS_ACCESS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
Hello Evan,
I tested your recommendation and it did not work. I then removed the outside ACL and modified inside ACL to just allow access to the box for management and the NAT and again it did not work. I also then removed the inside / private ACL and it still does not work.
I tried with backup image NV3140A-R11-10-5-E.biz with same results.
Do we have a simple document that is current with such simple user case that I can refer to?
I am not a GUI person, so next step for me to try the GUI wizard that I will attempt after my dinner.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
I did a factory reset, used wizards and I still have the same issue. The wizard added a no rpf-check on the public policy side, as well as changed the cipher and hashing algorithms etc, and I can again connect via VPN, but no traffic flows.
I am using latest available Shrewsoft IPsec client on a windows 10 laptop and I can successfully VPN into a Cisco ASA and a Cisco Router without any issues.
Can someone please share a working Remote Access VPN configuration by masking the sensitive / private information on a 3100 series router?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
Finally, I saw my ping traffic crossing the VPN tunnel.
I was trying to first keep the things simple. I had no user authentication (XAUTH) and I was keeping remote-id to be any, so that any client that dials in using PSK will connect with the intention to add on XAUTH as a next step and then also add a matching remote-id in the firewall. Despite both end configuration to be correct, and tunnel establishing, the traffic will not flow.
So first I added a test user, then added a aaa authentication login list and used that list name under the IKE policy for client authentication and then changed shrewsoft Authentication tab to Mutual PSK+XAUTH and tried again. Still no go.
I then changed phase 2 / IPsec policy lifetime to be 1 hr from default 8 hours (28800 does not show up in CLI being default) and that made the whole thing work. So I thought somehow SA lifetime has some quirks.
Did a reboot of the firewall and the client laptop and I was able to get VPN work after these reboots.
Remember client end will always need to have a local ID, which I set up just a name. Then I added the matching ID as remote ID in firewall IKE policy and disconnected and reconnected and traffic flowed fine again. Did both ends reboot again to make sure my VPN is still working.
Then I changed the SA lifetime back to defaults and I found that pings stopped working. Reboot both ends and no luck. Changed SA lifetime back to 3600 at both sides and still no luck. Did reboots again, and with no change.
Deleted configuration and re-created the same config and it worked. And again played with the SA timings and things again break down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: IPSec Remote Access VPN - No Traffic
I have opened the case with support and they are looking into it.
I was testing with windows 10 with VPN client and second laptop I have is windows 7. I get these intermittent and unexplained issues with VPN connectivity as described above.
Just occurred to me and I installed VPN client on windows 7 laptop and tested with that and I don't have these issues anymore. But I have to figure out as customer now has mainly windows 10 laptops. I will try uninstall and then install of Shrewsoft in windows 7 compatibility mode and that might work, as it appears now that issue is on the VPN client side, not the router config.
Evan had mentioned that the client is not listed tested for windows 10, but I have tested today with 7 other clients who all have Cisco ASA or Cisco routers set up as IPsec VPN and on every single of those from the same test laptop, it works fine, only we seem to have some issue with Adtran router, may be firmware compatibility for use of this client on windows 10, when it worked fine for windows 7.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Finally the problem is solved for me;).
I re-installed Shrewsoft latest client using windows 7 compatibility mode and everything is working consistently.
Thank you Wil and Evan for your great support.