- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 5000 Series
- :
- Re: Network Advice/Help Needed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good Afternoon,
My company is closing in on our transition to our new facility. We have our existing DS3 circuit plugged into our NetVanta 5305 router. At our new location, we’ll have just 2 different segmented LAN’s one for contracts and one for Headquarters. I’m trying to figure out what will be more efficient and secure moving forward. My main goal is to completely segment the two LAN’s with access to both only from the admin level. If that’s not possible I can always run a second computer for network access to the other LAN if need be. Another important factor is that we will have a diverse dedicated backup line from another ISP but it will be handed over as an Ethernet cable not a BNC connector requiring a T3 wide module. I don’t believe we’ll have to worry about load balancing as the DS3 should be fine; our primary concern is having a dedicated backup line on a failover setup in the case Verizon goes down.
Scenario 1:
Have the NetVanta 5305 as the Gateway Router at the edge of the network. I would utilize only ETH 0/1 port and plug a SnapGear 560u router in behind the NetVanta. The SnapGear 560u has builtin firewall applications as well. I’ve configured this piece to have the primary and secondary Internet feeds. I can program the primary port to the NetVanta 5305 and then have the fail safe/secondary dedicated line in place on the secondary port which would feed directly to our other ISP. The SnapGear 560u has 5 Ethernet ports which I’ve converted 2 of them to dedicated Internet Ports (1 for the NetVanta (Verizon) and 1 for secondary ISP). The other 3 ports will act as LAN segmentations which will point directly to the Primary Line.
Scenario 2:
This scenario relies totally on the NetVanta 5305 as the gateway router and firewall solution with Dell managed switches behind it using VLAN’s. My question in this scenario is how I utilize my secondary dedicated line on the NetVanta 5305. Are there any tutorials on programming the NetVanta 5305 for Failover and secondary lines? I’m assuming that the line would have to be plugged into the ETH 0/2 line and then configured on the GUI. ETH 0/1 would point to the internal switches.
Any help or guidance is greatly appreciated!
Cheers!
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
That is a common question about default-route vs. default-gateway. The command you are referencing (ip default-gateway <ip address>) is only applicable if the unit is in bridge mode. Here is an explanation of default-route vs. default-gateway: https://supportforums.adtran.com/docs/DOC-2443
Levi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
- Thanks for posting your question on the forum!
Both scenarios would allow you to accomplish the goals you had in mind. The only question I would have regarding Scenario 1 is whether or not you would still want to restrict access to the 5305 itself. The reason I ask this is that you can leave the 5305's firewall off and simply manage all firewall functionality on the SnapGear 560u. However, if you plan on restricting access through the 5305 (i.e. admin access), then you would have the firewall function turned on for the 5305 and the SnapGear.
With Scenario 1, the failover, firewall, and VLANs would be controlled by the SnapGear. The 5305's functionality would simply be to terminate the T3 and pass of ethernet to the router behind it. You could turn off the firewall functionality on the 5305 and let it simply be a passthrough device. Also, as I mentioned above, you could also turn on the firewall on the 5305 to restrict admin access to it from the outside (or internally), however, the SnapGear would be the primary routing device in your network.
With Scenario 2, the failover, firewall, and VLANs would be controlled by the NetVanta 5305. You could keep your original T3 using the T3 module, and then terminate the secondary internet connection using the unused ethernet interface (ETH 0/2). The following guide explains how to set up WAN failover using network monitoring: Configuring WAN Failover with Network Monitor
in AOS I will add that if the primary internet connection is using HDLC, frame-relay, or PPP, then you can simply use floating static routes instead of network monitoring to configure the failover. However, keep in mind you will still need to configure the NAT rules accordingly. The introduction in the guide will explain this.
As far as the idea of segment the two LANs in the 5305, you could configure trunking between the 5305 LAN port (ETH 0/1) and the switch that plugs directly into it. The switch would be configured for those 2 VLANs. The following guide explains how to configure interVLAN routing on the 5305: Configuring InterVLAN Routing in AOS - Quick Configuration Guide
As I mentioned earlier, either scenario will work and it is really up to the network administrators preference how they would like to set it up. However, please do not hesitate to let us know if you have any further questions.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
So in the case of scenario one, if I leave the current configs the way they are, I should be protected from outside access to the admin configs correct?
Also, I have an additional question, in our new building that's being constructed, we have data port connections everywhere but there has been one request to have a wireless signal in a centrally located conference room. I know there are wireless options through the NetVanta 5305 but I don't really want to broadcast from that point outward. Is it possible and logical to run a data cable from our switch panels to a COTS wireless router located inside the conference room? I'd disable all DHCP functions on the router and set the IP address on the specified network needed pointing through the gateway of the specific network. Would this work? Do you see any compatibility options? Your help is greatly apprecated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
- I would have to see your current configuration to verify whether access is available from the outside to the NetVanta 5305, but if the firewall is disabled then anyone would be allowed to access the 5305 and view the configuration (assuming they had the credentials to log in). You can reply to this post with your configuration for us to review, but please remember to remove any information that may be sensitive to your network.
Regarding your wireless question, the NetVanta 5305 can only act as an Access Controller for a NetVanta Access Point (i.e. 150). Unless you have these NetVanta Access Points, the 5305 is unable to provide wireless. I cannot provide a recommendation on the setup or regarding the configuration a non-Adtran wireless router or access point. However, if there was a NetVanta Access Point in your network, you could run a cable from the switch in your LAN to the location you would like to place the wireless router or access point (assuming the distance does not surpass the cable's distance maximum. The NetVanta 5305 would act as the wireless Access Controller, but the wireless signal would not be bound by where the 5305 is located.
Please do not hesitate to let us know if you have any further questions.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
I have another question in regards to the segmenting of the networks through VLAN's. With my two physically separated LAN's that I'm joining together at one location, there will be no communication between the the two. Both networks have independent File Servers, Printers and Switches. By using the VLAN option with only the 5305, all I'll need to do is configure the trunking between the ETH 0/1 and the switch correct? Once I have the trunking configured, I can establish the 2 VLAN's needed and then just route accordingly. If there's no communication between the two VLAN's, would there be a necessity for interVLAN routing?
Your help is greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Please disregard my last comment. I'll need the interVLAN routing because I'm only trunking 1 line from the 5305 ETH 0/1 to the Managed Switch correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
- That is correct. You would be using ETH 0/2 for your secondary internet connection. The 5305 ETH 0/1 port would be set up as a 802.1q trunk to your managed switch. You would have the ability to restrict access between those VLANs by configuring your firewall if you would like. However, the 5305, since it has routing capabilities, would be able to route between your VLANs.
Let us know if you have any questions.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Are there any specific guides for the 5305 series for configuring the 802.1q trunk in the GUI? Or any guides in relation to that?
Thanks, I just want to make sure I put in the right configurations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
- The following guide explains how to set up intervlan routing on an AOS router: Configuring InterVLAN Routing in AOS - Quick Configuration Guide
Please do not hesitate to let us know if you have any questions.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
I've read through the InterVLAN Routing Guide and it's pretty straight forward.
I wanted to run my current information by you to see if you had any suggestions or if what I'm thinking will work. The two locations my company currently has right now are totally separate networks with different ISP's and Networking equipment. When we transition to our new building, the existing T3 line we have at location A will be transitioned. Having said that, the only network hooked into the 5305 right now is our location A office set. They were setup as a Private LAN using the 192.168.0.X/24 subnet (We have about 60 users). The default gateway of the router is 192.168.0.1. Our Location B network was set up years ago on the 192.168.1.x/24 subnet and we have about 15 users.
Having said all that, outside of using the interVLAN routing to hook in both subnets, I do not want to have any communication between the two VLAN's. One VLAN will be our HQ setup, and the other VLAN will be our contract setup. I understand I'll need to identify the two VLAN's in the 5305 using the 802.1Q encapsulation. Should I set up two private Security Zones with no communication between them internally. Basically I'd just be setting rules for each VLAN to be able to access the Internet correct? Also, once I get past that, the current default gateway of the router is 192.168.0.1 should that be changed? I'm trying not to get ahead of myself, I have a pretty good understanding of what I need to do, I'm just trying to make the current configs work that we have, because they've been manually entered into each system.
So my questions from that:
- Do I need to change the default gateway of the 5305?
- I'll need to setup 2 VLAN with independent security zones with no communication between.
- We have Dell Power connect switches that can be managed, I'll just need to identify the two VLAN's and ports being used.
- Am I missing anything?
Your help is so greatly appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
In addition, does it make a difference which VLAN is selected as the Native VLAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Those are all great questions, and I will try to answer them in this post. First, let me say, that it sounds like you have all the concepts correct, but hopefully I can alleviate any confusion that you have.
I will start by addressing the NetVanta 5305 setup. If you would like to keep the networks separate, then primarily, everything would remain the same in theory and you will not setup "interVLAN routing." The HQ network would remain the same, with the additional aspect of being assigned a VLAN. So, on both the 5305 and the switch, they would need to be assigned a VLAN, such as VLAN 1 (for this example). Therefore, on the 802.1q trunk setup on the 5305 the HQ VLAN would be VLAN 1. Then on the switch, every port that connects to something in the "HQ network" will need to be assigned as VLAN 1 (a trunk port would connect the switch to the 5305). The concept will be the same for the "Contractor" subnet. You will assign it a VLAN sub-interface on the 5305 802.1q trunk port (VLAN 2 in this example). Then on the switch, every port that connects to something in the "Contractor network" will need to be assigned as VLAN 2.
The firewall will only need a source NAT statement so each network/VLAN can access the Internet. However, if you specifically want to deny the different networks/subnets from communicating to each other, then you can add an ACL above the NAT statement that blocks traffic between these two networks such as:
ip access-list extended BLOCK-LAN-LAN
permit ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255
ip access-list extended INTERNET-ACCESS
permit ip any any
ip policy-class PRIVATE
discard list BLOCK-LAN-LAN
nat source list INTERNET-TRAFFIC interface ppp 1 overload
The native VLAN is not important in this design, but it has to match throughout the network. By default most devices have VLAN 1 as the native VLAN. If you would like to leave VLAN 1 as the native, most likely the switch is already configured that way, it may reduce the time spent on configuration and network design/verification. The bottom line is, it doesn't matter what the native VLAN is, it just needs to match throughout the network.
Please, let me know what additional questions you have, and I will try to help in any way I can.
Levi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Hey Levi,
Thanks so much for your post. Setting the default VLAN to the Native was the only thing I was missing. I have all the VLANs up and running and set up DHCP for all so I could switch back and forth for testing purposes. I'm working directly through the WEB GUI and was trying to decipher your CMD Line above. I'm at the point where I have all VLANs working and connecting to the internet, but I still have inter communication between them. I'm currently able to access servers on VLAN 2 while sitting on VLAN 3 which is what I definitely have to block.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
The tricky thing right now is, I currently have our operational side plugged in and running off of the Eth 0/1 port. I'm doing all my testing on the Eth 0/2 port which has went very well. I just have to make sure any changes to the Firewall or ACL won't directly effect my current operational LAN as I'm testing.
Your help is greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
One more question sorry... Since my current operational LAN is setup on Eth 0/1 and is using the 192.168.0.x/24 subnet and is pointing to the overall gateway on the router, will I need to change my default gateway on the router itself? I'll have to change my current 192.168.0.x subnet to the VLAN which I haven't done yet because it's still in operation. Once I do that, I'm assuming I'll have to change the default gateway of the router for the Route Table.
I don't think it would be the correct config to have my next hop coming from 192.168.0.1 going to the default gateway of the router itself at 192.168.0.1, If I change that to something like 192.168.10.1, that should be okay correct? Your help is greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Hi Levi,
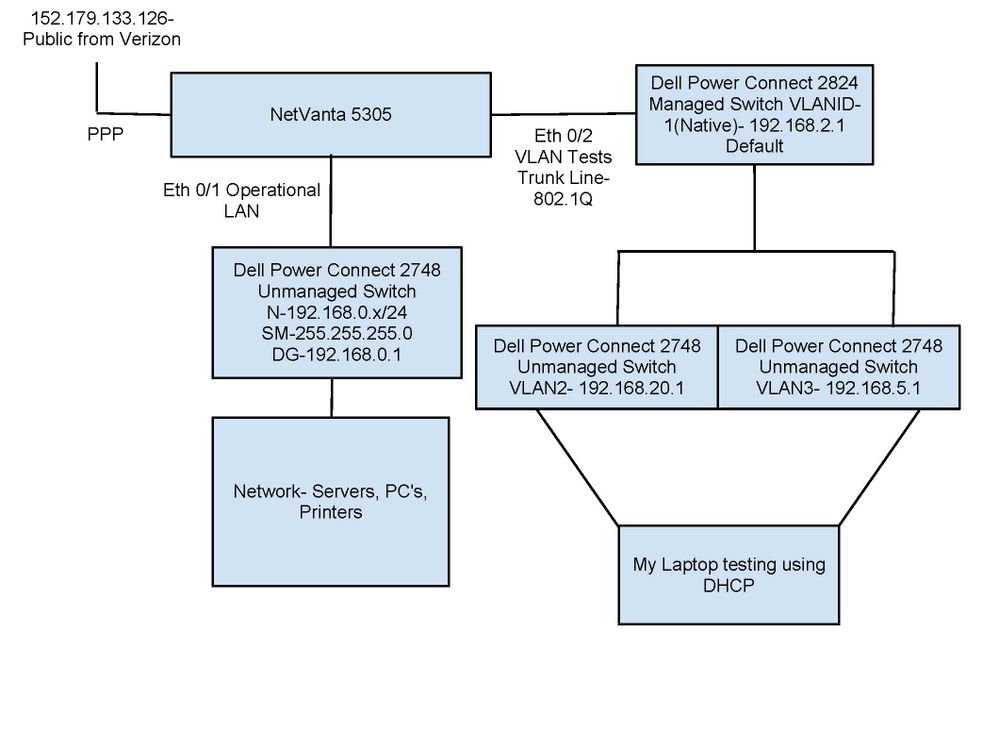
I'm attaching to JPEG images. One for the testing I'm currently doing and one for the final configurations once testing has been completed and our offices have been moved.
Hopefully this will assist in my questions in regards to the default gateway. Also, the CMD line instructions you mentioned earlier, can that be done in the GUI by following the same functional thought?
Your help is greatly appreciated.
First Image is Current network diagram as of today and what I'm dealing with during testing. The second image is where I need to be once our move takes place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
In the current testing picture, I'm able to connect to servers and resources in the operational LAN which is what I need to be blocking. I don't want anyone to the ability to communicate or access resources between VLANs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Thank you for replying with the network diagram, but I did not receive the configuration. If you are still able to communicate between subnets, without seeing the configuration, most likely you have not added the discard list as I suggested previously. If you do not understand the CLI configuration commands I provided, then you can do it in the GUI:
Data > Firewall > Security Zones > "Private" > Add Policy to Zone 'Private' > Filter > Continue > Specified > 192.168.0.0 255.255.0.0 > Specified > 192.168.0.0 255.255.0.0 > Apply > Then you will need to make sure this newly created filter is above the source NAT statement
I'm not sure I follow the question about the default-gateway? Are you asking what should the default-gateway of the devices on the network be? They should most likely be pointed to the ADTRAN's LAN IP address as the default-gateway for the network.
Levi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Network Advice/Help Needed
Sorry about not having the configuration, I'm not at that location currently. I had to draw the diagram from memory.
I understand the CLI, it's just much easier to access the GUI in the way things are currently setup.
As for the default gateway question, in the current setup, the default gateway is not an issue. When I go to do the final network setup and configuration, I'm thinking I'll have to change the default gateway of the Adtran from 192.168.0.1 to something like 192.168.10.1 because my contracts VLAN will be 192.168.0.x/24. I'm assuming if I don't change the Adtran's DG I'll cause issues when routing because it will see them as the same correct?