- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Adtran Support Community
- :
- Discussion
- :
- NetVanta
- :
- NetVanta 7000 Series
- :
- Static one to one NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using the GUI. I attempted the following:
Create a one to one NAT Translation for both inbound and outbound traffic for an internal server on one of my vlans. I went into the DATA:FIREWALL and selected security zones. I then selected Public and added the following policies:
1. I created a static one to one inbound NAT Pool.
2. I created a static one to one outbound NAT Pool
3. I created a allow all policy.
Here is the config portion that pertains to that:
!
ip access-list extended web-acl-10
remark POB SERVER ALLOW
permit ip any host 12.69.x.x
!
ip access-list extended web-acl-11
remark POB SERVER OUT
permit ip any any
!
ip access-list extended web-acl-9
remark POB SERVER
permit ip any any
!
!
ip nat pool web-nat-pool-1 static
local 12.69.x.x 12.69.x.x global 172.16.1.50 172.16.1.50
!
ip nat pool web-nat-pool-2 static
local 172.16.1.50 172.16.1.50 global 12.69.x.x 12.69.x.x
!
ip policy-class Private
allow list self self
nat source list wizard-ics interface eth 0/0 overload
!
ip policy-class Public
nat destination list web-acl-9 pool web-nat-pool-1
allow list web-acl-10
nat source list web-acl-11 pool web-nat-pool-2
!
Is this correct? Will this work or should I have done it a different way?
Thanks,
Message was edited by: matt - removed public IPs
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
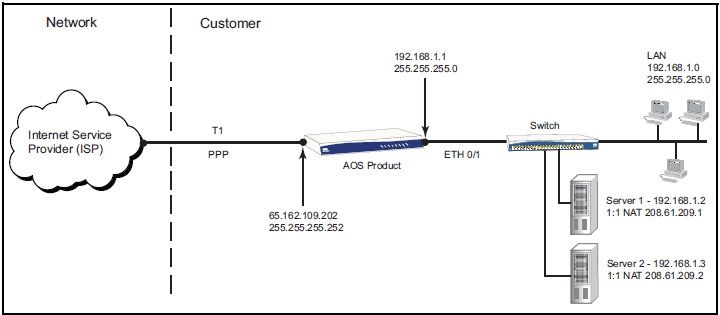
I would recommend configuring a 1:1 NAT as outlined in the guide instead of using NAT pools. Page 40 of the PDF has the following example:
Example 9 - One-to-One NAT
In this example, two separate one-to-one NAT rules are created for two servers on the private side of the AOS firewall. To accomplish this, the public IPv4 addresses that are used to access the servers (208.61.209.1 and 208.61.209.2) must be applied as secondary addresses to the WAN interface (PPP 1). On the Public ACP, nat destination list commands are used to match any traffic destined to these public IPv4 addresses and direct it to the corresponding internal servers (192.168.1.2 and 192.168.1.3). In the Private ACP, nat source list commands are used to match any traffic sourced from the specified servers and change its source address to the corresponding public IPv4 address. Any traffic not matching the first two NAT statements is caught by the catch-all NAT statement that provides Internet access to all of the other hosts on the LAN with the address 65.162.109.202. Administrative access is allowed for HTTPS and SSH by the Public ACP with the allow statement referencing web-acl-3. Administrative access is allowed on all available servers from the Private ACP with the allow list self self command because it references an ACL that matches all traffic.
!
ip firewall
!
interface eth 0/1
ip address 192.168.1.1 255.255.255.0
access-policy Private
no shutdown
!
interface t1 1/1
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface ppp 1
ip address 65.162.109.202 255.255.255.252
ip address 208.61.209.1 255.255.255.255 secondary
ip address 208.61.209.2 255.255.255.255 secondary
access-policy Public
no shutdown
cross-connect 1 t1 1/1 1 ppp 1
!
ip access-list standard wizard-ics
remark Internet Connection Sharing
permit any
!
ip access-list extended self
remark Traffic to NetVanta
permit ip any any log
!
ip access-list extended web-acl-3
permit tcp any any eq https
permit tcp any any eq ssh
!
ip access-list extended web-acl-4
remark 1:1 NAT 208.61.209.1 > 192.168.1.2
permit ip any host 208.61.209.1
!
ip access-list extended web-acl-5
remark 1:1 NAT 192.168.1.2 > 208.61.209.1
permit ip host 192.168.1.2 any
!
ip access-list extended web-acl-6
remark 1:1 NAT 208.61.209.2 > 192.168.1.3
permit ip any host 208.61.209.2
!
ip access-list extended web-acl-7
remark 1:1 NAT 192.168.1.3 > 208.61.209.2
permit ip host 192.168.1.3 any
!
ip policy-class Private
allow list self self
nat source list web-acl-5 address 208.61.209.1 overload
nat source list web-acl-7 address 208.61.209.2 overload
nat source list wizard-ics interface ppp 1 overload
!
ip policy-class Public
nat destination list web-acl-4 address 192.168.1.2
nat destination list web-acl-6 address 192.168.1.3
allow list web-acl-3 self
!
ip route 0.0.0.0 0.0.0.0 ppp 1
!
Thanks,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
I would recommend configuring a 1:1 NAT as outlined in the guide instead of using NAT pools. Page 40 of the PDF has the following example:
Example 9 - One-to-One NAT
In this example, two separate one-to-one NAT rules are created for two servers on the private side of the AOS firewall. To accomplish this, the public IPv4 addresses that are used to access the servers (208.61.209.1 and 208.61.209.2) must be applied as secondary addresses to the WAN interface (PPP 1). On the Public ACP, nat destination list commands are used to match any traffic destined to these public IPv4 addresses and direct it to the corresponding internal servers (192.168.1.2 and 192.168.1.3). In the Private ACP, nat source list commands are used to match any traffic sourced from the specified servers and change its source address to the corresponding public IPv4 address. Any traffic not matching the first two NAT statements is caught by the catch-all NAT statement that provides Internet access to all of the other hosts on the LAN with the address 65.162.109.202. Administrative access is allowed for HTTPS and SSH by the Public ACP with the allow statement referencing web-acl-3. Administrative access is allowed on all available servers from the Private ACP with the allow list self self command because it references an ACL that matches all traffic.
!
ip firewall
!
interface eth 0/1
ip address 192.168.1.1 255.255.255.0
access-policy Private
no shutdown
!
interface t1 1/1
tdm-group 1 timeslots 1-24 speed 64
no shutdown
!
interface ppp 1
ip address 65.162.109.202 255.255.255.252
ip address 208.61.209.1 255.255.255.255 secondary
ip address 208.61.209.2 255.255.255.255 secondary
access-policy Public
no shutdown
cross-connect 1 t1 1/1 1 ppp 1
!
ip access-list standard wizard-ics
remark Internet Connection Sharing
permit any
!
ip access-list extended self
remark Traffic to NetVanta
permit ip any any log
!
ip access-list extended web-acl-3
permit tcp any any eq https
permit tcp any any eq ssh
!
ip access-list extended web-acl-4
remark 1:1 NAT 208.61.209.1 > 192.168.1.2
permit ip any host 208.61.209.1
!
ip access-list extended web-acl-5
remark 1:1 NAT 192.168.1.2 > 208.61.209.1
permit ip host 192.168.1.2 any
!
ip access-list extended web-acl-6
remark 1:1 NAT 208.61.209.2 > 192.168.1.3
permit ip any host 208.61.209.2
!
ip access-list extended web-acl-7
remark 1:1 NAT 192.168.1.3 > 208.61.209.2
permit ip host 192.168.1.3 any
!
ip policy-class Private
allow list self self
nat source list web-acl-5 address 208.61.209.1 overload
nat source list web-acl-7 address 208.61.209.2 overload
nat source list wizard-ics interface ppp 1 overload
!
ip policy-class Public
nat destination list web-acl-4 address 192.168.1.2
nat destination list web-acl-6 address 192.168.1.3
allow list web-acl-3 self
!
ip route 0.0.0.0 0.0.0.0 ppp 1
!
Thanks,
Matt