Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Subscribe
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Adtran Support Community
- :
- Discussion
- :
- SmartRG
- :
- SmartRG (General)
- :
- Configuring IPSec
Anonymous
Not applicable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020
01:13 PM
Configuring IPSec
Purpose & Scope
This document provides instructions for setting up an IPSec connection.
Use Case
IPSec would be used in a case when added security is needed for a VPN connection. IPSec builds a tunnel through the Internet for a specific reason, like using VPN to telecommute. By using IPSec, your system is not contaminated by security risks occurring on the open Internet.
Steps
- Connect your PC to your CPE via the Ethernet Cable.
- If downloading via the WAN interface, proceed to step 3.
- Enter the IP address of the CPE device (WAN or LAN) in your browser URL dialog box.
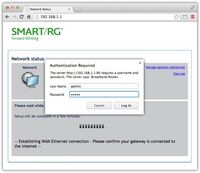
The default LAN IP is 192.168.1.1. The Authentication Required dialog box appears. - Enter your credentials.
The default User Name is “admin” and default Password is “admin”. If your modem has different login credentials, contact your ISP. The Network Status page of the modem appears. - Click Manage Gateway (Advanced).
This link is either at the top right corner of the Network Status pane or at the bottom of the pane. The Device Info page appears. - In the left menu, click Advanced Setup > IPSec.
The IPSec page appears. - Click Add New Connection.
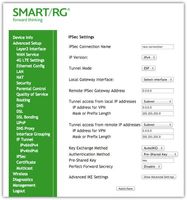
You can also remove currently set up connections. The IPSec Settings page appears. - Fill in the fields, using the information in the table below.
- Click Apply/Save.
This task is completed.
| Field Name | Description |
| IPSec Connection Name | Enter a descriptive name for this connection. |
| IP Version | Select the IP version environment associated with your infrastructure. Options are IPv4 and IPv6. |
| Tunnel Mode | Select the encapsulation method to be used. Options are:
|
| Local Gateway Interface | Select the WAN connection to be associated with this tunnel. |
| Remote IPSec Gateway Address | Enter the WAN IP address for this tunnel. |
| Tunnel Access from Local IP Addresses Tunnel Access from Remote IP Addresses |
Select IP information for sites A and B. Options are:
|
| Key Exchange Method | The key-exchange method to be used for IPSec. Options are:
|
| Authentication Method | Select the method by which the remote end will authenticate. Options are:
|
| Perfect Forwarding Secrecy | This setting determines whether a session key derived from a set of long-term keys is compromised if one of the long-term keys in the set is compromised.
Note: For SR515ac models, this field is named Perfect Forward Secrecy. |