- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello!
I understand that when coupled with a specific ACL you can capture packets moving through an AOS device. What is the procedure to accomplish this and are there any tips / tricks / cautions?
Thanks,
Dan
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Dan,
From the command line, we have the ability to look at every packet coming in and out of the router, along with the ability to limit that debug with an access-list. This is best done from a telnet or SSH session, as the console can drop some of the output due to a limited buffer size.
It is preferable to not have any other messages pop up that may interfere with the capture text. The events and any other debugs should be turned off before performing this debug. This can be done with the following commands:
Router# no events
Router# undebug all
The general command is:
<> = optional
Router# debug ip packet <access-list name> <detail / dump>
NOTE: It is not recommended to run this command without referencing an access-list. Therefore, create an extended access-list (ACL) that matches the traffic you want to capture. In this example the ACL, named CAPTURE, will select traffic both to and from the host 10.1.1.1 to be captured when the debug ip packet CAPTURE detail command is issued. (when enough traffic has been captured type undebug all to stop the capture)
---------------------------------------------------
To capture the traffic to and from a particular peer:
ip access-list extended CAPTURE
permit ip any host 10.1.1.1
permit ip host 10.1.1.1 any
debug ip packet CAPTURE detail
---------------------------------------------------
If you desire to see more than what 'detail' provides, choosing 'dump' will output the entire packet in text form. The output from the debug ip packet <access-list name> dump command can either be copied to a text document, if your terminal emulator scrollback is long enough to copy all the generated output, or you can use a logging session in the terminal emulator to save the output to a text file. This text file will eventually be converted to an actual packet capture.
The program Wireshark (www.wireshark.org) comes with a utility known as Text2Pcap. Copy (text2pcap.exe) from the Wireshark folder to a root drive, as well as the text file generated from the debug ip packet <access-list name> <detail / dump> command. Then run the following command from a DOS prompt:
text2pcap.exe -e 0x800 <Text Filename> <Capture Filename to Create (extension .pcap)>
The capture file can then be opened in Wireshark.
NOTE: If the unit is running a firewall, you will probably see every packet twice (once entering the firewall & once leaving, depending on the ACL you are using); the second may be after a NAT process if NAT is enabled. Furthermore, if the traffic is across a VPN, the second packet will not be seen since it enters/leaves the router encapsulated in VPN
If you have any further questions, please do not hesitate to reply to this post.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Not the Solution
- Report Inappropriate Content
Dan,
From the command line, we have the ability to look at every packet coming in and out of the router, along with the ability to limit that debug with an access-list. This is best done from a telnet or SSH session, as the console can drop some of the output due to a limited buffer size.
It is preferable to not have any other messages pop up that may interfere with the capture text. The events and any other debugs should be turned off before performing this debug. This can be done with the following commands:
Router# no events
Router# undebug all
The general command is:
<> = optional
Router# debug ip packet <access-list name> <detail / dump>
NOTE: It is not recommended to run this command without referencing an access-list. Therefore, create an extended access-list (ACL) that matches the traffic you want to capture. In this example the ACL, named CAPTURE, will select traffic both to and from the host 10.1.1.1 to be captured when the debug ip packet CAPTURE detail command is issued. (when enough traffic has been captured type undebug all to stop the capture)
---------------------------------------------------
To capture the traffic to and from a particular peer:
ip access-list extended CAPTURE
permit ip any host 10.1.1.1
permit ip host 10.1.1.1 any
debug ip packet CAPTURE detail
---------------------------------------------------
If you desire to see more than what 'detail' provides, choosing 'dump' will output the entire packet in text form. The output from the debug ip packet <access-list name> dump command can either be copied to a text document, if your terminal emulator scrollback is long enough to copy all the generated output, or you can use a logging session in the terminal emulator to save the output to a text file. This text file will eventually be converted to an actual packet capture.
The program Wireshark (www.wireshark.org) comes with a utility known as Text2Pcap. Copy (text2pcap.exe) from the Wireshark folder to a root drive, as well as the text file generated from the debug ip packet <access-list name> <detail / dump> command. Then run the following command from a DOS prompt:
text2pcap.exe -e 0x800 <Text Filename> <Capture Filename to Create (extension .pcap)>
The capture file can then be opened in Wireshark.
NOTE: If the unit is running a firewall, you will probably see every packet twice (once entering the firewall & once leaving, depending on the ACL you are using); the second may be after a NAT process if NAT is enabled. Furthermore, if the traffic is across a VPN, the second packet will not be seen since it enters/leaves the router encapsulated in VPN
If you have any further questions, please do not hesitate to reply to this post.
Thanks,
Noor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Text to .pcap
Noor,
Thanks for your detailed use of the text based packet capture.
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Text to .pcap
For future reference, AOS has the ability to perform a more user friendly packet capture than the methods described above. With the Packet Capture feature built in to AOS, you no longer have to perform the tedious steps to convert .txt to .pcap. This can all be done by the AOS device.
Please, review the Configuring Packet Capture in AOS document for additional information.
Levi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Text to .pcap
Thanks Levi. Appreciate the follow-up.
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Text to .pcap
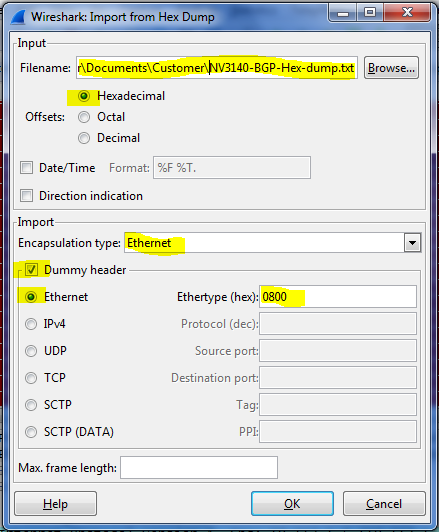
I found the command line for text2pcap.exe importing of the debug dump was not liking spaces in filenames and directories, and I didn't have paths set so I had to specify specific paths. So I tried it via the GUI like this. Seems to give the same result.
File -> Import from hex dump...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Accept as Solution
- Report Inappropriate Content
Re: Text to .pcap
also, it's a good idea to remove the "undebug all" text hidden in the debug output. Not 100% sure it was what caused wireshark to struggle on the decode once, but worth mentioning just in case.